The Alarming Acceleration of Supply Chain Attacks: From Nx to Qix in Just 13 Days

The software supply chain has become one of the most dangerous battlegrounds in cybersecurity. What used to feel like rare events now happen in rapid succession, and each new incident seems to carry greater impact than the last. Over the course of just thirteen days, we witnessed two compromises that reveal how quickly attackers are adapting and how fragile the trust in open source ecosystems truly is.
It started in late August 2025 with the compromise of the Nx build system. With more than 4.6 million weekly downloads, Nx is a critical part of many modern development pipelines. Attackers pushed malicious versions of the package into npm, and within hours developers around the world were unknowingly pulling in code designed to steal SSH keys, authentication tokens, and even cryptocurrency wallets. What stood out in this attack was not only the scale but also the tools. Reports showed that the attackers used artificial intelligence assistants like Claude and Gemini to automate reconnaissance and speed up data theft. In less than four hours, the malicious versions were taken down, but the damage to trust was already done.
Before the ecosystem could even catch its breath, a second and even more impactful attack struck. On September 8, 2025, a phishing email found its mark. A maintainer of some of the most widely used npm packages, unknowingly handed attackers the keys to the kingdom. Once inside, they injected malicious updates into eighteen different repositories, including chalk, debug, and ansi-styles. That number has already grown to 20 as investigators uncover the full scope of the compromise. Collectively, these packages see over 2.6 billion downloads every single week. This was no longer a targeted theft of developer credentials. This was an assault on the very foundation of open source, with billions of potential victims targeted downstream.
At the same time, the conditions for exploitation were more specific than they first appeared. An application would only have been compromised if it performed a fresh install on Monday, September 8, 2025, between approximately 9:00 AM and 11:30 AM Eastern Time, during the short window when the malicious packages were live. In addition, the project’s package-lock.json had to be created during that timeframe, and the vulnerable packages needed to exist in either direct or transient dependencies. These constraints, while still serious, narrow the set of impacted applications significantly.
The lesson is hard to ignore. In just under two weeks, the world moved from a supply chain breach that impacted millions to one that reached billions. The first relied on AI-powered automation. The second relied on deceiving a human being. Both worked. And both revealed the same uncomfortable truth: the attack surface is no longer just the code we write but the people who maintain it and the trust we place in them.
Organizations can no longer afford to treat supply chain security as a checkbox. The defenses must be as continuous as the threats themselves. Software bills of materials (SBOMs) and vulnerability exploitability data (VEX) need to be a standard part of procurement and development practices, so that when compromises happen, exposure can be identified in minutes and, not in days or weeks. Dependencies must be monitored in real time, not scanned once and forgotten. Developers must be supported with training to recognize phishing and social engineering. And threat intelligence must become contextual and actionable, because drowning in alerts helps no one when the next breach lands.
To help track the scope of the most recent compromise, below is a table of affected packages. This will be updated with the package URLs and GHSA advisories as disclosures continue to expand.
What these two incidents tell us is that supply chain attacks are not isolated anomalies. They are part of a pattern that is accelerating. The gap between incidents is shrinking. The scale of impact is growing exponentially. And the techniques are evolving to blend automation with human deception.
The future of software security will be decided by how quickly we adapt. Transparency, automation, and resilience are no longer optional strategies. They are the only path forward.
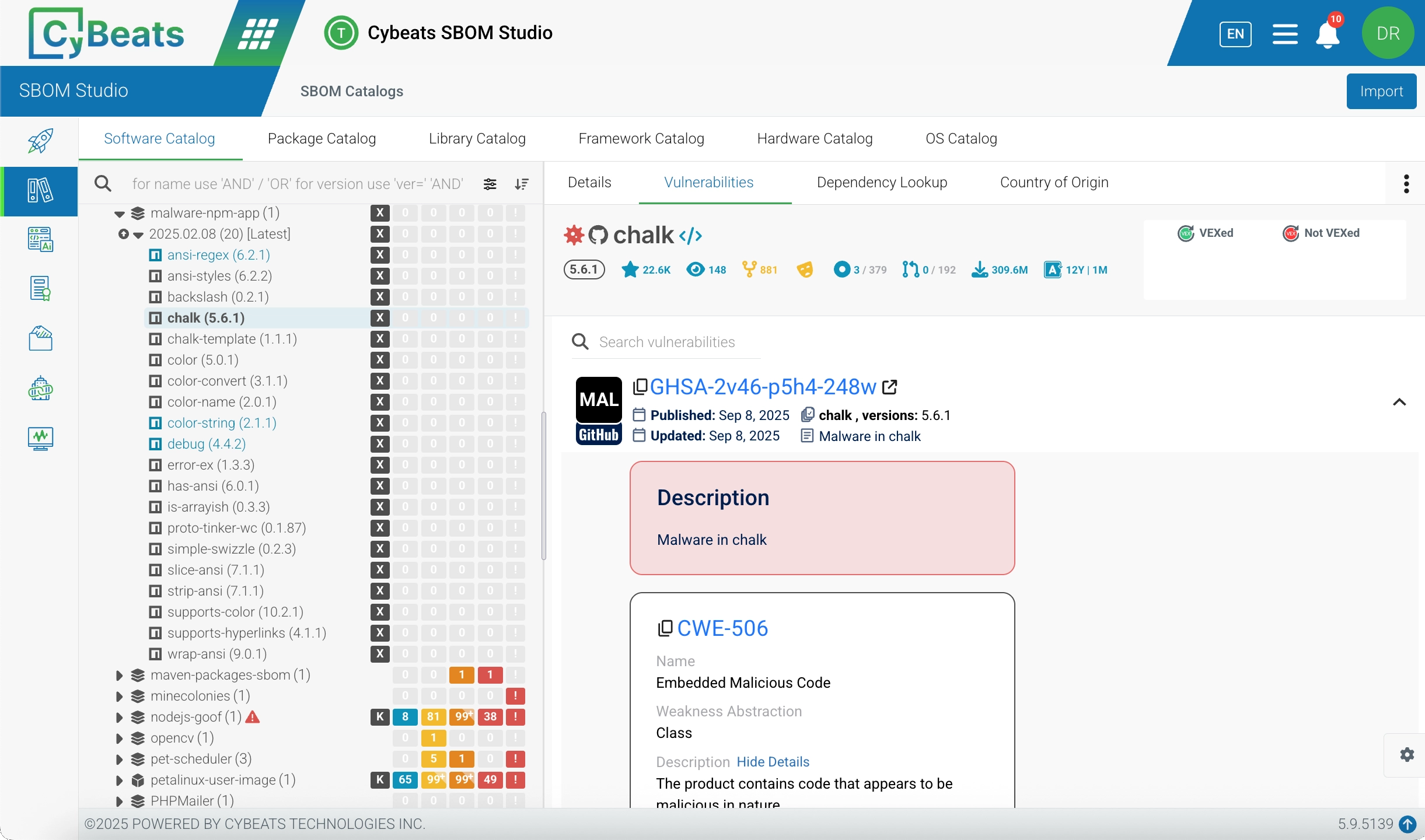
We detected the first indicators of compromise within hours of the malicious packages being published to npm repo. Our platform became aware of the threat through our continuous monitoring at approximately 10:20 AM EDT, well ahead of the first online notifications and LinkedIn posts covering the breach. This early warning gave our customers a critical head start to investigate and mitigate before the incident became broadly reported.
The coordinated response across maintenance teams, npm, and GitHub advisories proved to be the critical factor in containing the impact of this incident. By acting quickly and transparently, they transformed what could have escalated into a widespread security event into a contained and manageable issue. This exception in response not only safeguarded the ecosystem but also demonstrated the importance of timely communication and decisive action in reducing risk at scale.
.svg)
See Cybeats Security Platform in Action Today
We shortened our vulnerability review timeframe from a day to under an hour. It is our go-to tool and we now know where to focus our limited security resources next.
.svg)

SBOM Studio saves us approximately 500 hours per project on vulnerability analysis and prioritization for open-source projects.
.svg)


.svg)
.svg)